In October of 2019 a small business received a suspicious email where the cyber criminal was posing as a client/customer of the organization. They sent the small business an email with a link attachment disguised as an Adobe document download. The firm was able to recognize a few key warning signs in the email and promptly reported the email as phishing.
Below we have included the spear phishing email as well as a real Adobe email for comparison. Take a look and see if you can identify some of the warning signs.
Adobe Document Cloud Email
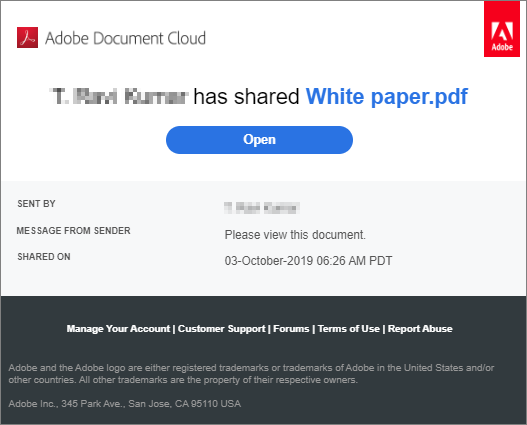
Phishing Email
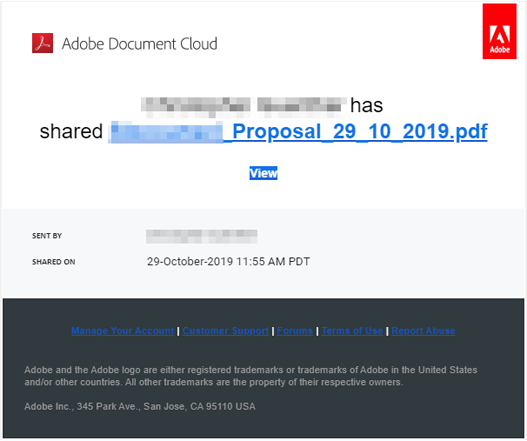
Can You Spot The Warning Signs?
While maybe not immediately obvious, once you know what to look for, the warning signs are easy to spot.
In this email the first thing that should tip you off is the call to action button. A call to action button is a large graphic designed to provoke an immediate response. Even if you are unaware of what an Adobe email should look like, the call to action in the phishing email is small and underwhelming. The suspicious nature of the call to action button should be a redflag to take extra caution with this email.
The second item that should cause you to raise an eyebrow is the links at the bottom of the email. These links appear in blue on the phishing email. A professional company, especially a creative software company like Adobe, will produce emails that are easy to read with text that stands out from the background. Poor design and difficult to read email graphics can be a sign that the email did not come from a reliable source.
Although not included in the screenshots above, another major warning sign the firm recognized was the lack of a recipient listed on the email. When the firm received the email there was no recipient listed in the "To" field of the email.
While these warning signs are subtle, they can help you determine if the email needs to be approached with caution. Next, ask yourself, do I know the person sending this email? Is the email address accurate? Am I expecting a file or link from them? If the answer is no, don't click.
When in doubt, use an alternative contact method to ask the sender if the email is from them. Either give them a call or send an email to an address that you are confident is safe. Do not reply to the email.
What Happens Next?
Report The Event
If you suspect an email is a phishing scheme, report the email as such. Most Email service providers give you the ability to report suspicious email as Phishing or Spam. You can also forward the email to reportphishing@apwg.org or report it to the Federal Trade Commission at ftc.gov/complaint. After reporting the email, block the email sender or manually move the email to spam.
Contact Your Client
If the phishing scam was impersonating a client, customer, or someone you know, reach out to them and inform them of the scam. They may have a security breach on their end that needs to be handled.
On the other hand, if you become aware of a scheme impersonating you or your business, contact all your clients. Make them aware of the breach what is being done to combat the cyber threat. Warn them of the malicious email and remind them not to click on any links or send any personal information via email.
Change Your Password
Regardless of whether the phishing scam was sent to you, or "from" you, change your passwords. If you have any contact with a cyber threat or phishing scheme, it is best practice to change your email password. The moment it takes to change your password is worth the potential hours spent combating a cyber breach.
Unfortunately phishing scams have been on the rise and cyber criminals are becoming increasingly sneaky. But, with the proper awareness, education, and protocol, you can avoid becoming their next victim.
